Other optional components
These components can be installed and work with Nuix Adaptive Security but are not required.
Kafka
Kafka is a widely-used open source event streaming platform. By configuring Nuix Adaptive Security to populate Kafka with events, the Nuix Adaptive Security data is streamed, collected, and analyzed along with your organization’s data.
If your organization is already using Kafka, see the Nuix Adaptive Security Administration Guide for information about configuring Nuix Adaptive Security to send events to Kafka.
If this is the first time your organization is using Kafka, we recommend installing the following:
Confluent Platform using Docker
Note: If the hostname of the machine that runs Kafka does not match its DNS name, add an entry to %SYSTEM32%\drivers\etc\hosts with the hostname and IP of the Kafka machine.
SSL with Kafka
SSL encryption is required for Kafka integration with Nuix Adaptive Security. You may need to modify the server properties on Kafka to accept SSL. Configure Kafka to have an SSL listener and provide the port of the SSL listener to Nuix Adaptive Security. Also provide the Kafka CA public certificate for the SSL listener.
Example
Note: The text in the example is commented out by default. You will need to uncomment the code to use it.
At the top of the config/server properties, enter the server name:
advertised.listeners=PLAINTEXT://<server name>:9092,SSL://<server name>:9093
At the bottom of config/server.properties:
Ensure the passwords and paths are correct for your environment.
Add the following line:
security.inter.broker.protocol=SSL
Splunk
Splunk helps to gather real-time data into a repository where it can be used to generate a visual representation of the data, such as graphs, reports, alerts, dashboards, and visualizations.
If your organization is already using Splunk, add Nuix Adaptive Security alerts to your Splunk feed to visualize Adaptive Security data in Splunk.
If you are using Splunk for the first time, use the following instructions to install Splunk and integrate it with Kafka:
https://docs.splunk.com/Documentation/Splunk/
See the Nuix Adaptive Security Administration for information about configuring Adaptive Security with Kafka.
Configure Splunk
Use the following steps to set up an instance of Splunk to test connectivity with Nuix Adaptive Security. Consult the Splunk documentation for more settings and configuration options.
Nuix Adaptive Security requires an HTTP Event Collector in Splunk.
To set up the HTTP Event Collector in Splunk:
Install Splunk Enterprise.
Browse to https://[splunk ip]:8000. Login with the admin account and password.
Go to Settings > Data inputs > Http Event Collector > Global Settings.
Verify SSL is enabled.
Verify the HTTP Port is 8088.
Create a new token.
Select HTTP Event Collector.
Enter a name like "Adaptive".
Ensure that Enable indexer acknowledgment is disabled.
Select Next.
Source type
Select Source Type Structured json_no_timestamp.
Create an index for every event type that will be forwarded. The indexes will be the base name and the view to be forwarded. See the following index list with the default base name of 'nuix_adaptive":
nuix_adaptive_alerts
nuix_adaptive_media
nuix_adaptive_file
nuix_adaptive_session
nuix_adaptive_print
nuix_adaptive_process
nuix_adaptive_keylog
nuix_adaptive_screenshot
nuix_adaptive_url
nuix_adaptive_clipboard
Add the created items to the Selected Item(s) box.
Review.
Submit.
Provide the token value and URL to Nuix Adaptive Security so it can forward events.
The Splunk URL should be "https://[splunk ip]:8088” if you followed the steps above.
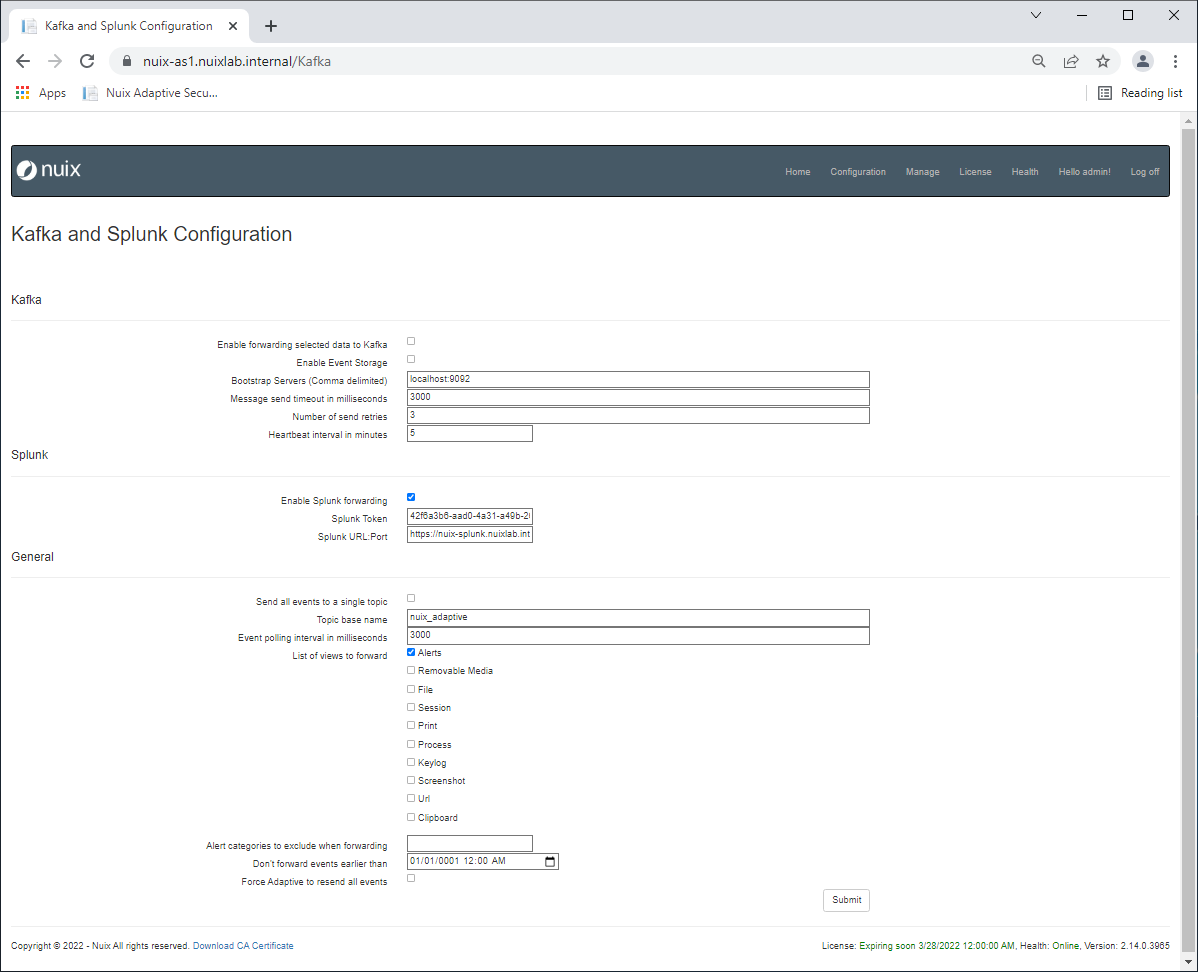
To configure Splunk:
Configure the Splunk service on each Primary and Secondary server using the Nuix Adaptive Security web interface. Nuix Adaptive Security requires the following from Splunk:
Token value
URL and port in a format such https://nuix-splunk.customer.name:8088.
To search for Nuix alerts from Splunk:
Set index="nuix_adaptive_alerts"