Nuix Adaptive Security endpoint agent installation
The Nuix Adaptive Security endpoint agent is installed on the endpoints. In the Nuix Adaptive Security application, create the configuration to define the agent settings. Then install the agent on an endpoint.
Most customers will export the agent installer from the Nuix Adaptive Security application. The agent installer is then deployed to an endpoint manually or via an enterprise management tool. An agent that was exported from the application has a configuration file embedded in the installer. The exported agent installer will have a name that begins with Nuix<OS>EndpointInstaller where OS is the platform followed by the agent version, date, and identification number. For Windows, the installer is a .exe and for Mac, the installer is a .zip file.
Agent installer file examples:
Windows: NuixWinEndpointInstaller_2_8_1_2016-release__20210304-154457.exe
Mac: NuixMacEndpointInstaller_2_8_0-636_ 20210210-234600.zip
Using SSL/TLS with a Nuix Adaptive Security installation
Secure Socket Layer/Transport Layer Security (SSL/TLS) is an industry-standard encryption method. SSL/TLS replaces any public or private key encryption used by an agent. Nuix Adaptive Security uses SSL/TLS by default.
This method is compliant with the Federal Information Processing Standards (FIPS). The same Certificate Authority (CA) certificates can also be used for multiple servers, while still using different server keys or certificates. The certificate and the Subject Common Name can be set in the Servers section of the configuration.
For more information about the servers and configuration, see the Nuix Adaptive Security User Guide.
For information about how to install SSL, see Installing SSL in Appendix D: Install Troubleshooting.
Install the agent with an enterprise management system
If an enterprise management system is continually installing the agent, any agents that were upgraded to newer versions from the Nuix Adaptive Security application will roll back to the version that is deployed by the enterprise management system. However, the embedded configuration within the installer will be overridden by the configuration that is assigned by the server providing the version rules are compatible.
For example, a company installs Nuix Adaptive Security version 2.6.1. The enterprise management systems are set up to deploy a 2.6.1 agent with an embedded configuration that includes 2.6.1 rules. Subsequently, the customer upgrades the system to 2.8.1 and using the Nuix Adaptive Security application upgrades the endpoints to 2.8.1. If the enterprise management system is not updated, it will re-deploy the 2.6.1 agent. If the configuration on the server has rules that are compatible with the 2.6.1 agent, the new agent will override the configuration. If not, the agent will operate with the embedded configuration.
Agent configuration
There are two parts to the agent configuration. The first part is set up in the System module. This is where you will do the system settings for the initial configuration. Once configured, these settings are not likely to change very often. The second part is the configuration settings which are more dynamic and can change throughout the investigation process. Manipulate the logic rules to go from broad to very targeted rules for specific endpoints or groups of endpoint.
The configuration module is where you can make dynamic changes to agents by manipulating the rules in real time. The configuration defines the agent settings, logic rule set, namespaces, and hash lists.
If the agent configuration is for a Mac or Linux operating system the parameters are different.
For agent configuration details and procedures, see Configuration in the Nuix Adaptive Security User Guide.
Windows agent deployment
The Windows agent provides endpoint security for Windows operating systems in your Nuix Adaptive Security environment. To view the supported Windows versions, see the system requirements for the Nuix Adaptive Security Endpoint Agent.
Install the Windows agent
The Nuix Adaptive Security endpoint agent can be pushed to endpoints by the IT department or installed manually through the command line. The agent must be installed as an administrator. For best results, make the agent a part of the standard build so that a separate deployment is not required.
For Windows systems, the agent configuration is embedded in the executable. Whether the agent is installed from the command line manually or using an enterprise management tool, the following qualifiers apply when executing the installer. Typically, customers will use the -i -e when installing the agent.
| Agent Qualifiers |
Description |
| -i install or upgrade the agent service |
The -i will install the agent on a clean system or replace an existing agent regardless of the current agent version. |
| -e use the embedded configuration |
The -e installs the agent with the configuration embedded in the executable. |
| -u uninstall the agent service |
The -u will uninstall the agent regardless of the version. |
| -c, filename: use a configuration file |
The -c is not used in a typical deployment and imports a configuration from a file. |
The path and agent names are set on the first installation of the agent.
To install the agent on a Windows endpoint:
Copy the Endpoint Installer to the target endpoint.
Open an administrator command prompt.
Navigate to the directory containing the Endpoint Installer (for example, CD c:\configs).
Launch the Endpoint Installer file with the switches –i and –e after the installer name. For example, in the command prompt, type the following and then press Enter.
NuixEndpointInstaller_2_0_1_1813-release_Windows_Rules_20190812-160045.exe –i -e
After the agent installation is complete, the directory prompt returns. If there is an error in the installation, you will see an error window.
Note: When an agent loses network connectivity, the agent continues to run as defined by the configuration. When the agent reconnects to the server, the agent reports back, and uploads all of the collected data.
After a few minutes, verify that the agent is connected in the application on the endpoints tab.
Mac agent deployment
The Mac agent provides endpoint security for macOS in your Nuix Adaptive Security environment. To view the supported macOS versions, see the system requirements for the Nuix Adaptive Security Endpoint Agent.
For more information about agent configuration, see Configuration in the Nuix Adaptive Security User Guide.
macOS Apple endpoint security
Apple Endpoint Security is required by Apple for macOS 10.15.3 (Catalina) and above.
The agent will automatically use the EndpSec library. Once the agent is installed and running, the administrator will need to grant full disk access.
The Mac agent needs the following permissions.
The Mac agent must be granted full disk access in the Mac security settings to operate properly.
The Mac agent must be granted screen recording permission to use the screen shot feature.
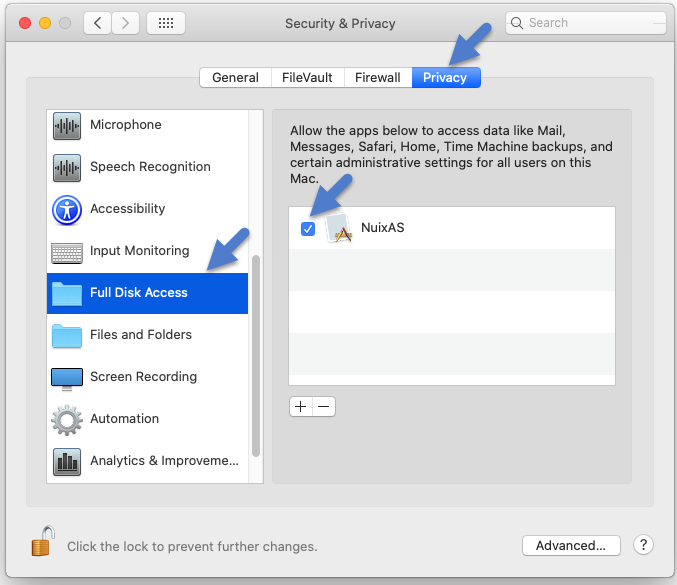
To grant full disk access on a Mac:
On the Mac, open System Preferences and go to the Security & Privacy settings.
Select the Privacy tab and scroll down to Full Disk Access.
Select the check box next to NuixAS in the app list, as shown in the following image. If NuixAS is not in the list, click the "+" button below the list and add the agent application, which is located at /Library/Nuix/Endpoint/NuixAS.
macOS kernel extensions (KEXT) security
KEXT Security is required by Apple for macOS 10.13 (High Sierra) to 10.15.2 (Catalina).
Apple requires user approval when installing a KEXT for the first time, and a dialog box appears, such as the one shown in the following image.
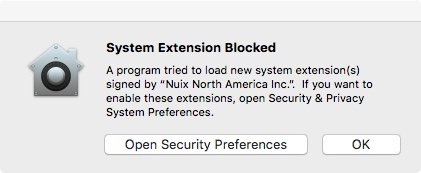
When this alert is dismissed by clicking Open Security Preferences or OK, the installer reports success but the KEXT is placed in a limbo state, pending user input. The agent is started by the installer normally but reports in the log that it cannot connect to KEXT. The agent continues to run normally, but process events are severely restricted until the KEXT is loaded. For example, the agent is not able to properly block processes. There is no notification of exactly when the user approves the KEXT. As a result, the agent tries to connect every 15 minutes until succeeding.
User approval of the KEXT is done through System Preferences, in the Security & Privacy window.
Install the Mac agent
For Mac systems, the zip file contains a .pkg file and a .bin file which contains the configuration. The .pkg file must run from the same directory as the .bin file. You can run the .pkg file manually or use an enterprise management system.
Requirements
Installation requires an admin password.
The Mac agent needs the following permissions.
The Mac agent must be granted full disk access in the Mac security settings to operate properly.
The Mac agent must be granted screen recording permission to use the screen shot feature.
To install the agent on a macOS endpoint:
Copy the Installer file to the target endpoint.
Double-click the pkg file to launch the installer or run the pkg file from the command line.
If using the command line option, enter the following:
sudo /usr/sbin/installer -target / -pkg NuixEndpointInstaller-vX.X.X.pkg
If there is a problem with the installation, check the Nuix install log file at:
/var/log/nuix/nuixAS_install.log
View the installer application log file at:
/var/log/install.log
Linux agent deployment
The Linux agent provides endpoint security for Linux operating systems in your Nuix Adaptive Security environment. To view the supported Linux operating systems, see the system requirements for the Nuix Adaptive Security Endpoint Agent.
Note: If you install the Linux agent on an unsupported Linux version, it might install successfully but the agent will run with limited functionality.
Install the Linux agent
To download and install the agent on a Linux endpoint:
Note: The installation requires root privileges.
Place the .run file on the endpoint.
Install the Linux agent from the endpoint command line by running the .run file. The default .run filename contains the version number, and identification number so the command is in the following format:
sudo ./NuixLinEndpointInstaller_X_X_X-XXX_<date>_<id>.run
The Linux agent is installed into three file directories by default.
/opt/nuix
/var/lib/nuix
/var/log/nuix
/var/opt/nuix
These directories are configurable during installation by modifying the .run script.
To verify that the Linux agent was successfully installed, check the "service manager" via systemctl:
sudo systemctl status nuixas.service
This will return "active (running)" for the Active value upon successful installation.