Set decryption keys and a Word List of passwords
The Decryption Keys tab of the Evidence Processing Profile or Edit Processing Profile window, (depending on how you access either window), allows you to:
Manage Word Lists of passwords
Configure the keys and key passwords to use when processing files
Set a Word List of passwords
Decrypt PGP email and S/MIME emails This section also covers information about:
Item decryption of emails
Password discovery using a password bank
About item decryption of emails
To decrypt emails during processing, you must configure the keys and any associated passwords beforehand. You can also reprocess encrypted items after they are identified, and can add the keys to key management prior to reprocessing.
When encountering an encrypted email, Nuix Workstation reads private keys from its configured key ring collections or key stores and when it finds the item’s matching key ID in the collection or store, it decrypts the email. A key ring is a directory of known encryption keys or public keys.
Note: You can only access encrypted mail files if both the Nuix Workstation key and password for the encrypted file are correct.
BitLocker decryption
Nuix Workstation uses Microsoft’s built-in encryption tool, BitLocker to decrypt and filter encrypted forensic images before processing data. BitLocker also provides a complete audit trail of the image.
You should enter user passwords and recovery keys in the password bank. There is no way to assign passwords to particular encrypted images. As a result, all passwords in the bank are tried against each encountered encrypted image.
PGP/Symantec and McAfee Drive decryption via Passware (disk image)
Nuix Workstation integrates with Passware to allow decryption of encrypted disk images and containers using user names and passwords provided in a Word List. Nuix Workstation can decrypt and filter forensic images before processing data using PGP/Symantec and McAfee Drive via Passware. This allows you to maintain your evidential integrity by allowing a complete audit trail of the image.
You should enter user passwords and recovery keys in the password bank. There is no way to assign passwords to particular encrypted images. As a result, all passwords in the bank are tried against each encountered encrypted image.
Note: Only users with a licensed installation of Passware Kit Forensic 2022 can access this functionality to decrypt files in Nuix Workstation. Nuix Workstation automatically recognizes the Passware license in the background to allow decryption. The System Diagnostics dialog has information on dependencies tovalidate if Passware is detected.
File formats supported for decryption
Nuix Workstation supports decrypting the following file formats:
PGP emails, including:
RFC822 emails with OpenPGP standard MIME content
‘Inline’ PGP-encrypted bodies and attachments
Loose PGP-encrypted items with both binary and ASCII armor
Emails in the MAPI family of containers such as MSG, PST, Exchange Web-Services, EDB
S/MIME emails, including:
S/MIME content encapsulated in emails of RFC822
Emails in the MAPI family of containers, like MSG, PST, Exchange Web-Services, EDB, and others.
IBM Notes (NSF) mailbox
Mail Xtender volumes (EMX files) eamil archive
HCL Notes, HCL Domino, or Lotus Notes emails (NSF files)
Decrypt PGP and S/MIME emails
Nuix Workstation decrypts PGP-encrypted and S/MIME-encrypted emails during processing if the appropriate keys and passwords are provided. (While Lotus Notes, Entourage, and OLM email containers may contain PGP-encrypted and S/MIME-encrypted content, Nuix Workstation currently does not support encrypting that content from those containers.)
To decrypt PGP emails, import keys as key ring collections from both ASCII-armored and binary files. To decrypt S/MIME emails, import keys as:
Key ring collections from both ASCII-armored and binary files
Key store files with .p12 or .pfx extensions
This section details how to do the following:
Add a key ring collection to decrypt PGP emails
Add key store files to decrypt S/MIME emails
Add a key store file to decrypt Mail Xtender volumes
Add a regular expression to decrypt Mail Xtender volumes Decrypt HCL Notes emails with an HCL Notes ID file
Decrypt HCL Domino emails with an HCL Domino ID file Decrypt Lotus Notes emails with a Lotus Notes ID file
Add a key ring collection to decrypt PGP emails
To add a key ring collection to decrypt PGP emails:
Open the Evidence Processing Profile window or the Edit Processing Profile window. See Open the Evidence Processing window in Configure Evidence Processing settings.
Select the Decryption Keys tab.
Click Add KeyStore and select the files you want to add.
The keys added to the Decryption Key Management list display the following information:
Unique Identifier: A unique key ID (the last few digits of the fingerprint of the key). It allows you to distinguish multiple keys and subkeys of the same user in a key ring collection.
User ID: A user's email address, name, or any unique string that identifies the user to PGP.
Key Type: For PGP, the key type is PGP/MIME key ring.
Password: Where you enter a password for each key.
Enter the passwords for the keys and click OK to save changes.
Add key store files to decrypt S/MIME emails
To add key store files to decrypt S/MIME emails:
Open the Evidence Processing Profile window or the Edit Processing Profile window. See Open the Evidence Processing window in Configure Evidence Processing settings.
Select the Decryption Keys tab.
Click Add Keystore and select the files you want to add.
Click Open to open the Enter Password dialog.
Key store files are password-protected at the file level.
Provide the necessary password for the key store file allowing it to be added to the Decryption Key Management list. The keys found in the key stores are added to the Decryption Key Management list, and display this information:
Unique Identifier: The S/MIME key alias.
User ID: The friendly name configured for the key, if any.
Key Type: For S/MIME, the key type is PKCS#12 File.
Password: Where you enter one for each key store or for a store-level S/MIME key store.
Add a key store to decrypt Mail Xtender volumes
You can encrypt EMC Mail Xtender archives with ICE 128-bit or 64-bit encryption. Nuix Workstation allows you to associate Mail Xtender key store volumes (.emx extension) with the password required to decrypt them.
To add a key store file to decrypt Mail Xtender volumes:
Open the Evidence Processing Profile window or the Edit Processing Profile window. See Open the Evidence Processing window in Configure Evidence Processing settings.
Select the Decryption Keys tab, and click Add Keystore.
Select a Mail Xtender volume file (this is the same file that will be added as evidence to the case).
The Mail Xtender volume identifier is read from the selected file and added as an entry to the password table.
In the Key Password field, enter the password for the file.
Repeat these steps for other volumes you want added to the case evidence.
Add a regular expression to decrypt Mail Xtender volumes
If you prefer, you can specify a regular expression and apply the same password to all volume identifiers that match that regular expression. To add a regular expression to decrypt Mail Xtender volumes:
Open the Evidence Processing Profile window or the Edit Processing Profile window. See Open the Evidence Processing window in Configure Evidence Processing settings.
Select the Decryption Keys tab, and click Add Password Regex.
From the Data type menu, select Mail Xtender.
In the Regular expression field, enter a regular expression search string. The simplest one that matches all volume identifiers in a case is “.*”.
In the Password field, enter the password to apply to all volumes that match the regular expression.
Click OK.
Decrypt HCL Notes emails with an HCL Notes ID file
You can import HCL Notes ID files and map them to NSF mail stores in evidence. To decrypt encrypted NSF files, you require Notes ID files and their corresponding passwords. Nuix Workstation supports NSF file encryption at either the mailbox or message level.
To decrypt HCL Notes emails with an HCL Notes ID file:
Open the Evidence Processing Profile window or the Edit Processing Profile window. See Open the Evidence Processing window in Configure Evidence Processing settings.
Select the Decryption Keys tab.
Click Add HCL Notes ID to open the HCL Notes ID File Mapping dialog.
In the NSF file field, specify the encrypted NSF file name you want to associate with an ID file, and (optionally) the complete path of the file name.
In the ID file field, browse to the location of the corresponding ID file.
In the Password field, enter the corresponding password for the ID file.
Click OK.
Decrypt HCL Domino emails with an HCL Domino ID file
You can import HCL Domino ID files and map them to NSF mail stores in evidence. To decrypt encrypted NSF files, you require Domino ID files and their corresponding passwords. Nuix Workstation supports NSF file encryption at either the mailbox or message level.
To decrypt HCL Domino emails with an HCL Domino ID file:
Open the Evidence Processing Profile window or the Edit Processing Profile window. See Open the Evidence Processing window in Configure Evidence Processing settings.
Select the Decryption Keys tab.
Click Add HCL Domino ID to open the HCL Domino ID File Mapping dialog.
In the NSF file field, specify the encrypted NSF file name you want to associate with an ID file, and (optionally) the complete path of the file name.
In the ID file field, browse to the location of the corresponding ID file.
In the Password field, enter the corresponding password for the ID file.
Click OK.
Decrypt Lotus Notes emails with a Lotus Notes ID file
You can import Lotus Notes ID files and map them to NSF mail stores in evidence. To decrypt encrypted NSF files, you require Notes ID files and their corresponding passwords. Nuix Workstation supports NSF file encryption at either the mailbox or message level.
To decrypt Lotus Notes emails with a Lotus Notes ID file:
Open the Evidence Processing Profile window or the Edit Processing Profile window. See Open the Evidence Processing window in Configure Evidence Processing settings.
Select the Decryption Keys tab.
Click Add Lotus Notes ID to open the Lotus Notes ID File Mapping dialog.
In the NSF file field, specify the encrypted NSF file name you want to associate with an ID file, and (optionally) the complete path of the file name.
In the ID file field, browse to the location of the corresponding ID file.
In the Password field, enter the corresponding password for the ID file.
Click OK.
About Password discovery using a password bank
A password bank is a list of 'possible' passwords in a password repository used to decrypt password-protected files during discovery and processing. Password banks are used to decrypt files enabling you to manage password lists by manually adding or importing a Word List as a .txt file. When using a password bank, Nuix Workstation runs passwords against each encrypted document until it finds a match.
You use a password bank at the case level. Nuix Workstation supports the following formats to create and use a password bank:
Microsoft Office 2010+ (.docx, .xlsx, .pptx)
Microsoft Office pre-2010 (.doc, .xls, .ppt)
Adobe PDF documents (.pdf)
Zip archives (.zip)
7Zip archives (.7z)
Bitlocker
PGP/Symantec via Passware (Disk Image)
McAfee Drive Encryption via Passware (Disk Image)
FileVault2
FileSafe
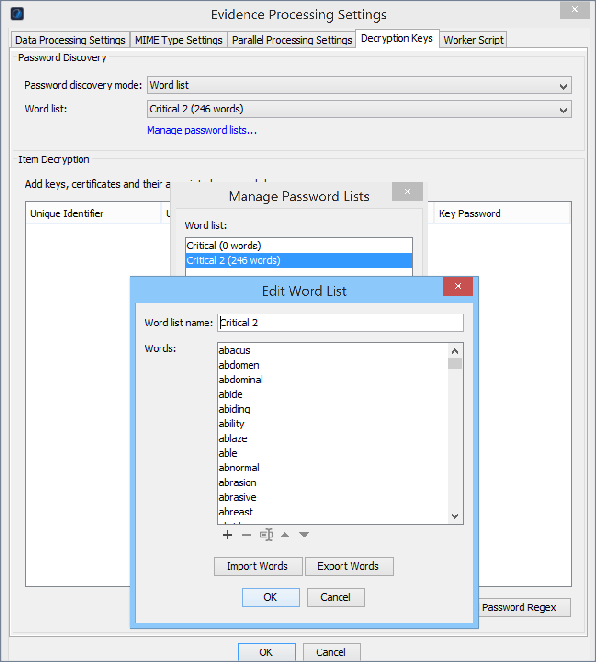
Manage password lists and keys for them
To manage password lists, and configure the keys and key passwords to be used when processing:
Open the Evidence Processing Profile window or the Edit Processing Profile window. See Open the Evidence Processing window in Configure Evidence Processing settings.
Select the Decryption Keys tab.
To manage how to use a Word List of passwords, under Password Discovery:
Use an existing Word List.
Create a new Word List from scratch.
Edit an existing Word List.
See the following Set the Word List for full details.
To add keys, certificates, and their associated passwords, under the About item decryption of emails section, see information for your specific email type.
Click OK to save your changes.
Set a Word List of passwords
To use an existing Word List of passwords, or to create or edit a new Word List:
Open the Evidence Processing Profile window or the Edit Processing Profile window.
See Open the Evidence Processing window in Configure Evidence Processing settings, and Create a Word List in Configure List types for repetitive processes for more information.
Select the Decryption Keys tab.
Under Password discovery, use the following top two options or only the last third option:
| Options |
Action |
| Password discovery mode |
None (default). If you want to add a word list, click Word list to enable its menu. You must select this each time you ingest or reload items. It is disabled by default because it is a time-consuming process. |
| Word list |
Select the Word Lists containing the list of passwords you want. Recommended: Keep a separate .txt file for each case. |
| Manage password lists |
Click this link to do the following: To edit a Word List, click + to open the Edit Word List dialog; and optionally: Add or delete words; and change their order. Click Import Words and select a .txt file of words to import into the Word List. Click Export Words to export the Word List to a specific location with a different filename if wanted.
To add a new Word List: Click + to open the Add Word List dialog. Specify its Wordlist Name. Click + to add a password to the Word List. On the Add Password dialog, enter the password and click OK. |